Cyberattacks have increased exponentially in the wake of the COVID-19 pandemic. No one is immune and no one is safe, which is why every company should conduct an on-site cybersecurity risk assessment. The Connectivity Center has partnered with several exceptional cybersecurity firms that specialize in cybersecurity risk assessments. Based on your specific needs, we can connect you to the firm that is your best fit.
Cyberattacks have increased exponentially in the wake of the COVID-19 pandemic. No one is immune and no one is safe, which is why every company should conduct an on-site cybersecurity risk assessment. The Connectivity Center has partnered with several exceptional cybersecurity firms that specialize in cybersecurity risk assessments. Based on your specific needs, we can connect you to the firm that is your best fit.
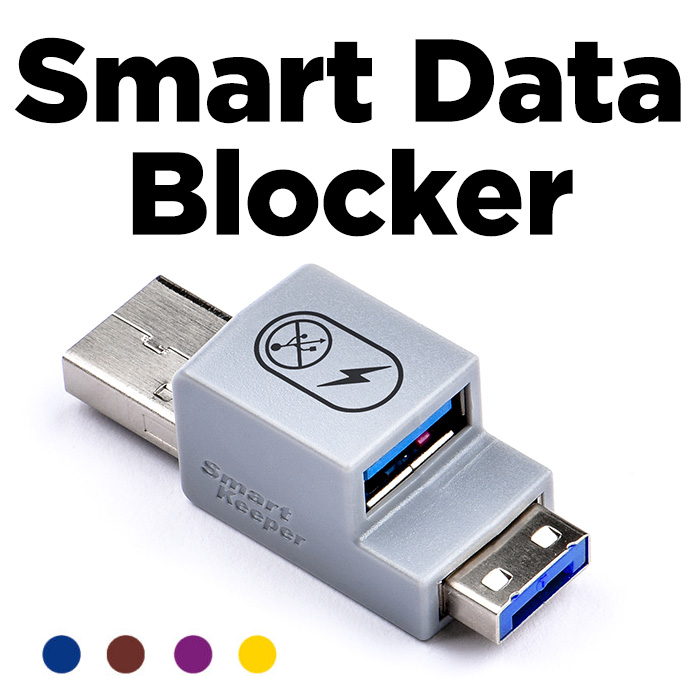
“The Smart Keeper USB port blockers have worked nicely to help secure computers used in our production facility.”
– Scott Adamy, Manufacturing Engineer

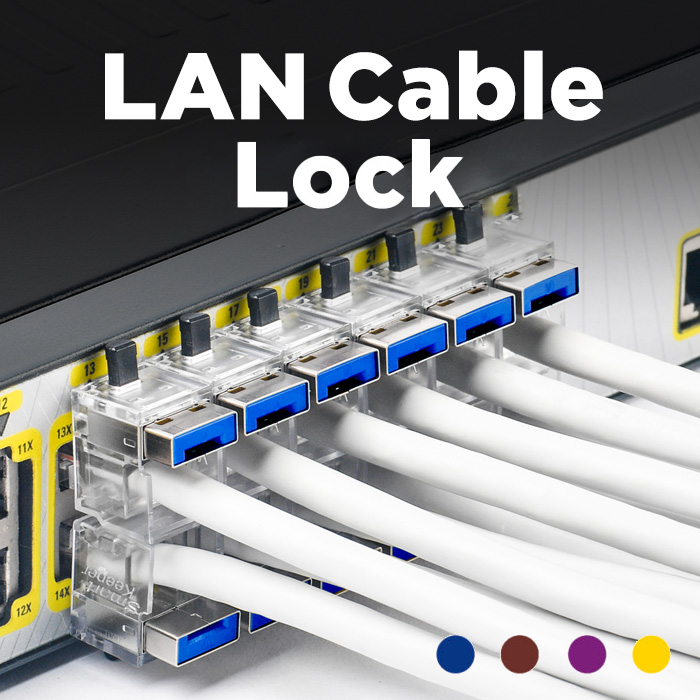
Trending Security Products
The top cyber-defense products in our store
More of What You’re Looking For
Check out our most popular categories based on our customers’ needs
Best Sellers
Our best-selling products are a great place to begin browsing our site. From rugged USB cables to the latest HDBaseT HDMI switches, these high-quality products exemplify the pride we take in our merchandise and what our loyal customers love about us. You’ll discover a vast array of products, including computer cables and KVM switches, AV equipment and networking products, and even system components and computer security products. We appreciate your business.
Thought Leadership
Read our recent blog posts for the latest in cybersecurity trends
Data Breaches in the Age of Extortion: Redefining Security Priorities
Sophisticated ransomware campaigns target sensitive data to extort large sums from organizations, with the added threat of publicly releasing confidential information.
USB Malware: The Silent Pandemic in Your Office
While cyber threats such as phishing or ransomware often dominate headlines, USB-based malware attacks are silently infiltrating organizations at alarming rates.
Your 2025 Cybersecurity Survival Guide
To stay secure amid changes in the cybersecurity landscape, it's important to stay ahead of the curve by implementing these strategies.
The Role of AI in Cybersecurity: Insights from 2024 Conferences
2024 U.S. cybersecurity conferences have shed light on AI’s pivotal role in predicting and preventing cyber-attacks, fundamentally shifting the paradigm from reactive to proactive defense strategies.